Scoring an old vulnerability
In 2021, we identified a flaw in the eduVPN server software, which we chose to report publicly through https://cveform.mitre.org/. This CVE can be briefly summarized as: arbitrary file read access for an authenticated user, and it was registered under the number: CVE-2021-41583.
Detailed summary of CVE-2021-41583
The vulnerability CVE pertains to an input validation issue in the vpn-user-portal 2.3.2 software, which became exploitable due to an update in one of the tools for generating QR codes. The vulnerability was present in Debian 10, Debian 11 and Fedora server software, but not in Debian 9 and CentOS 7. The attack could have been executed only by someone with user access to the eduVPN portal webserver. Via the exploit a user could get file system access as user “www-data” on Debian linux or user “apache” on Fedora. This could provide an attacker access the secret OAuth key. With such a key an attacker could impersonate another eduVPN user and get unauthorised access to VPN profiles.
How serious was this vulnerability?
Typically, vendors assign a score to CVEs to indicate the potential severity of the vulnerability. However, in our case, we had internal debates about what the suitable score level should be. Ultimately, we decided not to assign a vulnerability score to convey the impact.
We were recently approached by an institute using our software inquiring about the appropriate score for CVE-2021-41583. In the following section, we aim to clarify our perspective on the matter, employing the Common Vulnerability Scoring System as our basis.
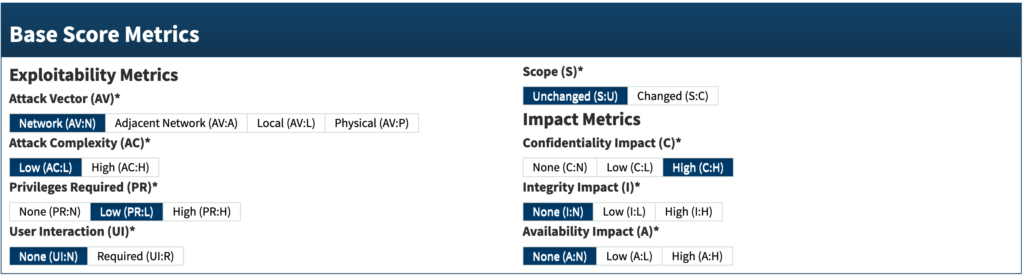
The Base Score Metrics consist of several components, which we will detail, focusing particularly on those that require explanation. The Attack Vector (AV) is defined as “network”. The Attack Complexity is categorized as “low”. The Privileges Required are “low”, given that an attacker merely needs a random user account. User Interaction is specified as “None”. The Scope is “Unchanged”, indicating that an attacker would only gain read access to the webserver’s files. Confidentiality Impact is rated as “high”, as an attack could potentially lead to unauthorized access to other users’ VPN profiles. Integrity Impact is “none”, as the vulnerability does not allow data modification. Finally, Availability Impact is also “none”, as the flaw does not impact system availability.
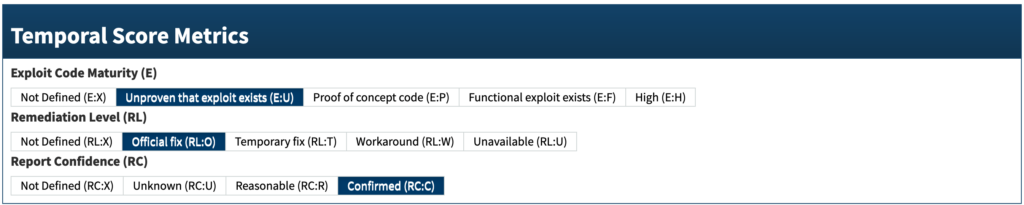
The Temporal Score Metrics also consist of a few components which we will be addressed. The Exploit Code Maturity is “unproven that exploit exists”. The Remediation Level is “Official fix”. The Report Confidence is “Confirmed”.
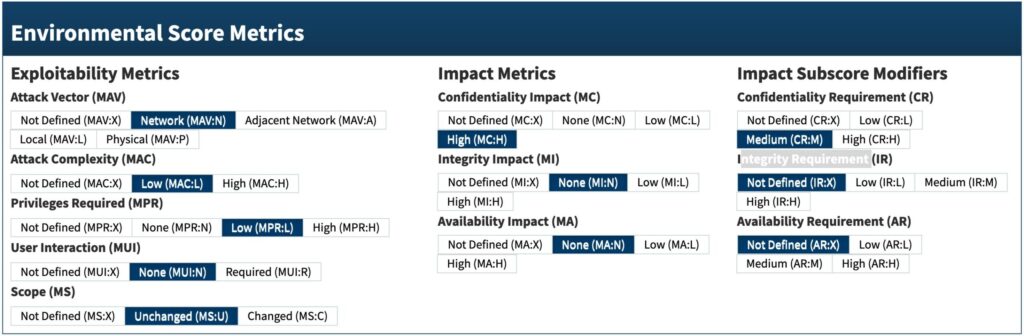
The Environmental Score Metrics consist of several components. The Attack Vector is “network”. The Attack Complexity is “low”. The Privileges Required is “low”. The User Interaction is “none”. The Scope is “unchanged”. The Confidentiality Impact is “high” as an attack could potentially lead to unauthorized access to other users’ VPN profiles. The Integrity Impact is “none”, because modification of data isn’t possible. The Availability Impact is “none”. The Confidentiality Requirement is “medium” because when an attacker would have access to other VPN users profiles it could do harm. The Integrity Requirement is “Not Defined” because there is no integrity risk. The Availability Requirement is “Not Defined” because there is no availability risk.
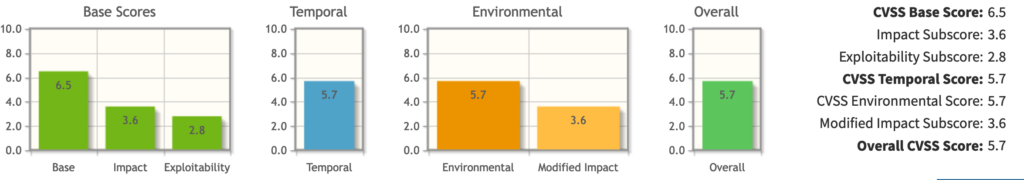
Based on the Common Vulnerability Score System Calculator the result is:
Summary
According to the CVSS calculator, the overall risk score for CVE-2021-41583 is 5.7, indicating that this vulnerability posed a moderate risk. The act of scoring the vulnerability now has highlighted the importance of including the CVSS classification. In future, the eduVPN team will incorporate this step during the initial publication while requesting a CVE, to provide a clear understanding of the risk level.


Add Comment